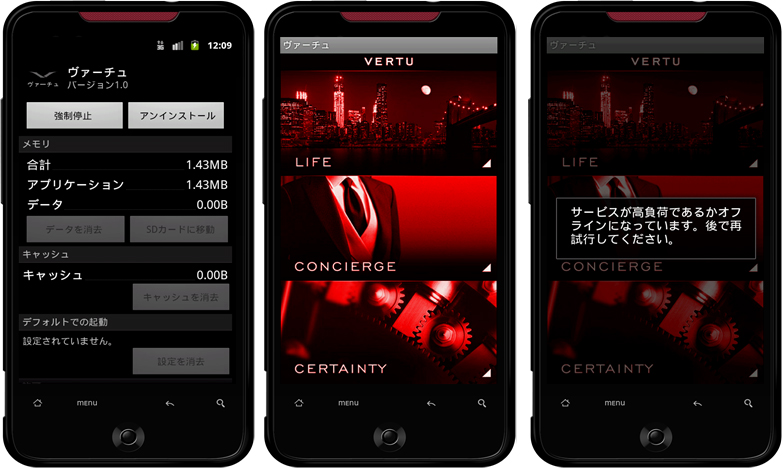
Last year we saw an attack targeting Android device users in which more than 2,400 malicious one-click fraud apps were published on Google Play in Japan. The attack has calmed down since October 2013, but it seems the scammers are still looking for opportunities to victimize smart device users in Japan.
Malicious Websites in Japan
As we enter 2014, McAfee has again discovered suspicious apps on Google Play in Japan. These apps lead users to malicious one-click-fraud websites. Ten apps have been published under one developer’s account, and the total number of downloads amounts to at least 5,000 as of this writing.
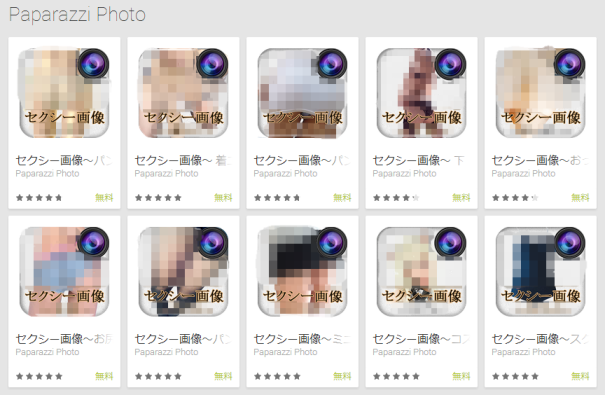
Figure 1: Suspicious apps lead users to malicious one-click fraud sites.
Unlike many apps discovered last year that simply displayed fraudulent websites, these new apps look harmless and behave just as adult image viewer applications. However, they enable a push notification from the attacker’s server based on GCM (Google Cloud Messaging) after their installation. The attacker can at any time send a push notification message containing a URL to a malicious one-click-fraud site, and users are sent to these risky sites via a browser once they tap on the message displayed on the system notification bar.
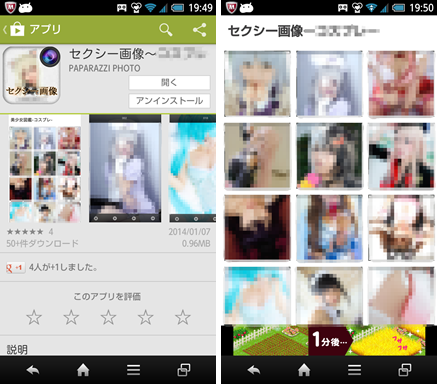
Figure.2: The apps implemented as an adult image viewer.
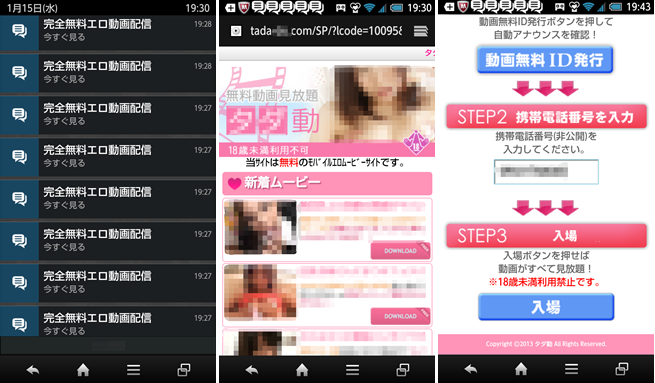
Figure.3: Push notification messages that lead users to a malicious one-click-fraud site.
The notification message is pushed once or twice per a day, and the destination URLs include not only one-click-fraud sites but also fraudulent adult dating service sites. Because this notification message is displayed even when the apps are not active and the origin of the message is intentionally undisclosed, it can confuse users in many cases and expose them to risks.
McAfee already reported Android/BadPush.A last year. This malware leads users to fraudulent adult dating services using push notification messages.
McAfee Mobile Security detects these newly found apps as Android/BadPush.B.
Tricking users into visiting one-click-fraud sites is not limited to Android apps on Google Play. Android adult apps on unofficial websites can also do this.
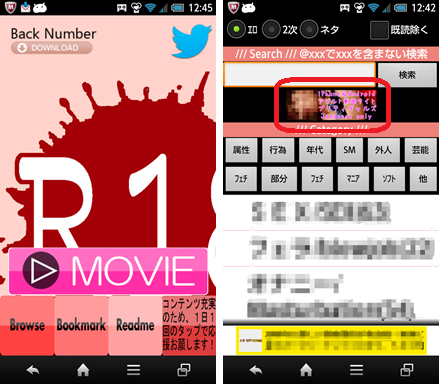
Figure.4: Examples of unofficial apps that lead users to one-click-fraud sites.
We have also confirmed that the scammers are tricking users on many Japanese blogs related to adult contents, as well as on Twitter, LINE, Kakao Talk, and others. Because these attacks are web-based, not only Android device users but also iOS device users should be careful.
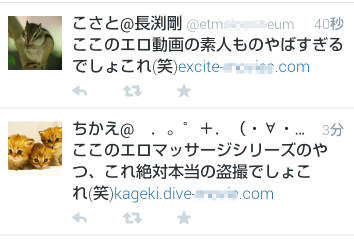
Figure.5: Tweets that lead users to one-click-fraud sites.
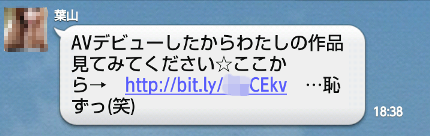
Fig.6: A LINE message that leads users to one-click-fraud sites.
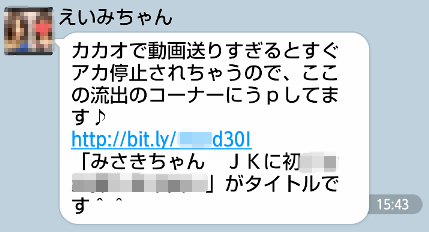
Figure.7: A Kakao Talk message that leads users to one-click-fraud sites.
McAfee Mobile Security detects this kind of Android app related to the scam activities as a variant of Android/OneClickFraud, and also blocks web browser access to such one-click-fraud sites on Android.
Although we can’t be sure that an attack on Google Play like last year’s will happen again, we can easily imagine that one-click scammers will continue to look for careless victims, lead them to malicious sites, and trick them into paying money using various tactics.
As always, users should ignore any approach from and payment request by scammers even if the users accidentally visit fraudulent websites and register for these services.